On the Cisco ISE, we can use Downloadable ACLs (DACLs) as an enforcement method to control what our endpoints are allowed to do in the network. These DACLs can be used with Catalyst switches and also with the Catalyst 9800 WLC starting with version 17.10.1
Compared to named ACLs, the main benefit of Downloadable ACLs is that we don’t have to configure them on every Network Access Device (NAD). Instead, the NAD can download them from the ISE on demand.
But how does the NAD get this ACL? Let’s explore this feature with the following setup:
The configuration on the ISE
On the ISE, the DACLs are configured on the PAN and get synchronized to the PSN as these nodes process the RADIUS communication with the NADs. The DACL is used in an Authorization Profile, which is used in the Authorisation Policy:
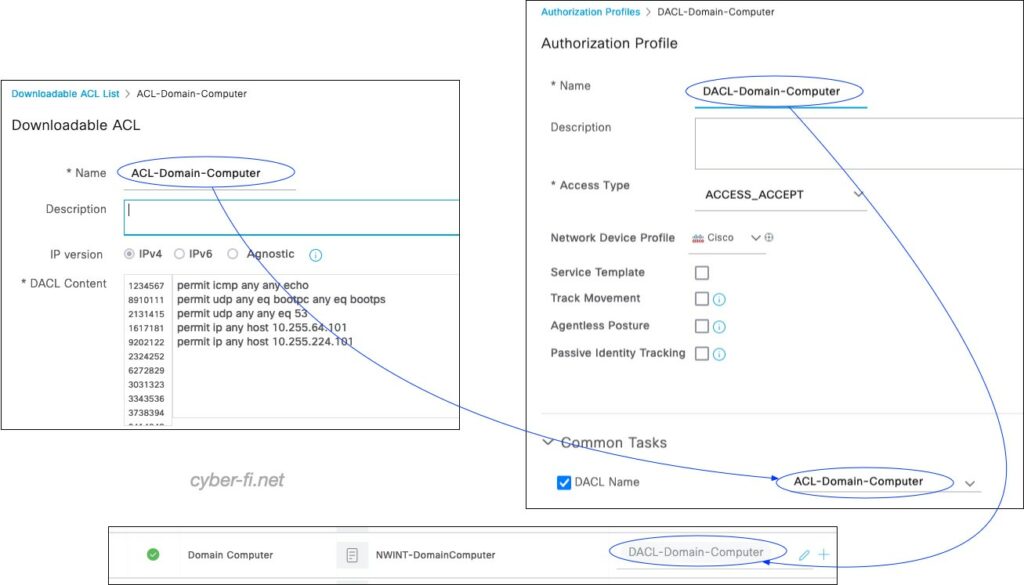
The Authorization
When the Domain PC logs on to the network, it authenticates with 802.1X and receives its authorization that is shown in the details of the ISE Live Log:
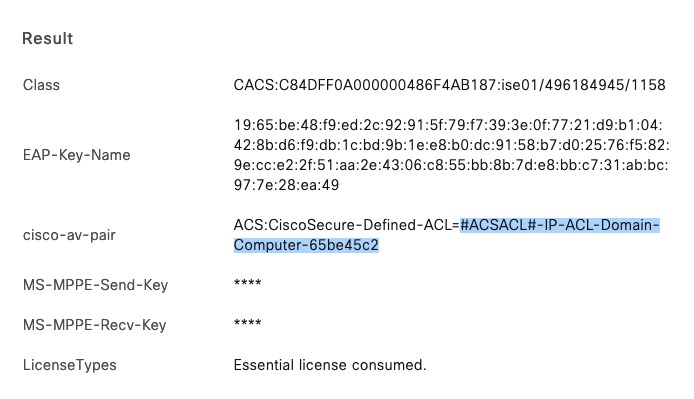
In this example, I only send the DACL as authorization. The ACL name gets a prefix of “#ACSACL#-IP-” to be distinguished from other ACLs on the NAD, and an appendix is used to tell the NAD that a DACL got changed and needs to be re-downloaded. This appendix looks slightly like a hash over the ACL, but it is likely only a hex number that increases in a Cisco-defined way. To analyze this number, I logged the names of the DACL.
This was the initial name on the DACL:ACSACL#-IP-ACL-Domain-Computer-65b4e84b
I changed the content of the ACL (I added one line), reauthenticated, and got a new name:ACSACL#-IP-ACL-Domain-Computer-65be44ec
Then I changed the ACL back to the original content (I removed the extra line), and the name changed again:ACSACL#-IP-ACL-Domain-Computer-65be45c2
The number didn’t change back to the first one, but instead kept increasing.
The RADIUS-Communication
This is the RADIUS communication between ISE and c9800:
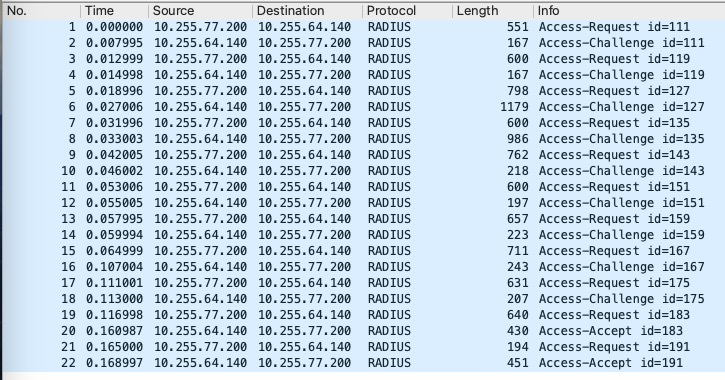
Packets 1 to 20 are the PEAP authentication with a final Access-Accept, in packets 21 and 22 we have the DACL download.
RADIUS packet 20
Cisco ISE sends an Access-Accept and adds the Vendor Specific Attribute (VSA) “Cisco-AVPair: ACS:CiscoSecure-Defined-ACL=” with the DACL name as the content. It has to be a VSA as this is a non-standard feature.
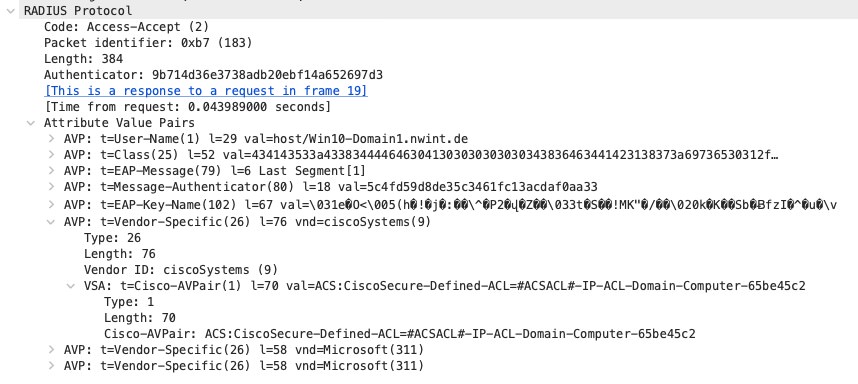
When the NAD receives this Authorization, it checks if this ACL has already been downloaded and cached. Then a new download would not be necessary.
RADIUS packet 21
My c9800 has not cached the DACL and triggers the Download with a new Access-Request to the RADIUS-Server:
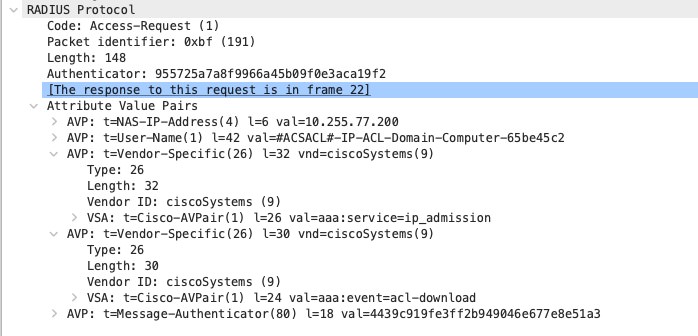
The NAD uses the RADIUS User-Name attribute to send the DACL name to the ISE. In addition to that, it adds the two VSAs “aaa:service=ip_admission” and “aaa:event=acl-download”
RADIUS packet 22
Next, the ACL is downloaded to the NAD:
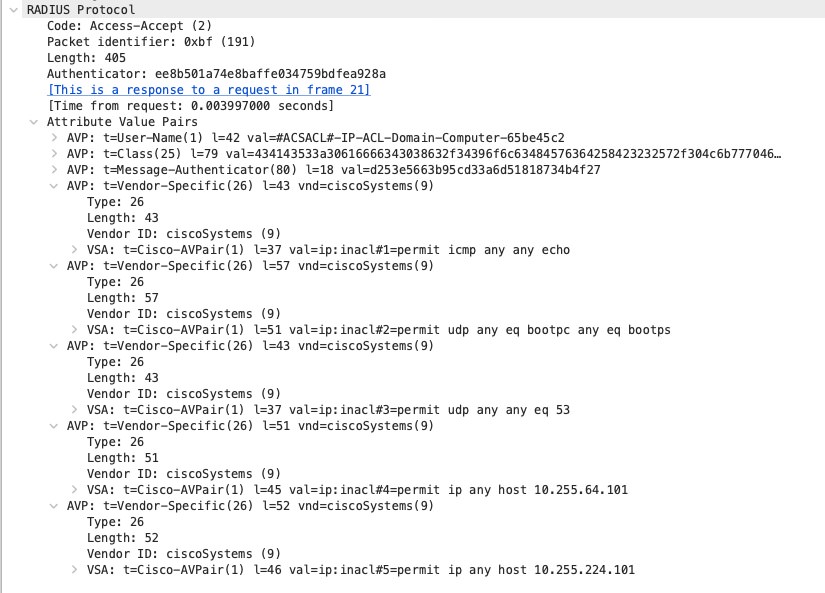
ISE answers with an Access-Accept that includes the ACL name in the RADIUS User-Name attribute and adds all ACL lines as numbered VSAs of type “ip:inacl”.
This DACL Download is show on the ISE as an additional Log entry:

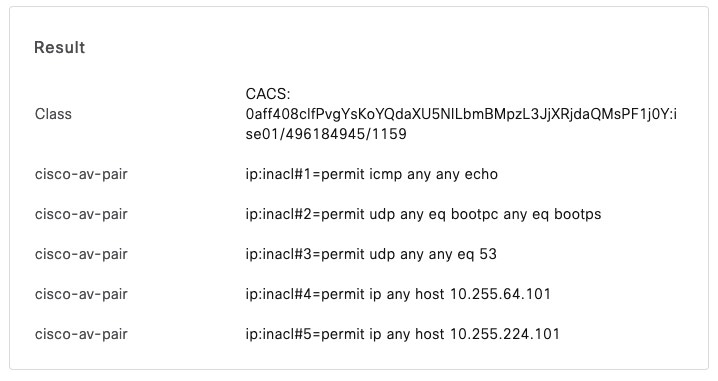
Happy ACL-downloading!
