In general, the Cisco ISE and Meraki devices play nicely together. But when doing 802.1X Authentication, the ISE hides some information and by enabling these, the Logs have a more relevant output.
Let’s start:
Vendor Specific Attributes
Meraki Devices send four Vendor Specific Attributes (VSA) in the RADIUS requests:
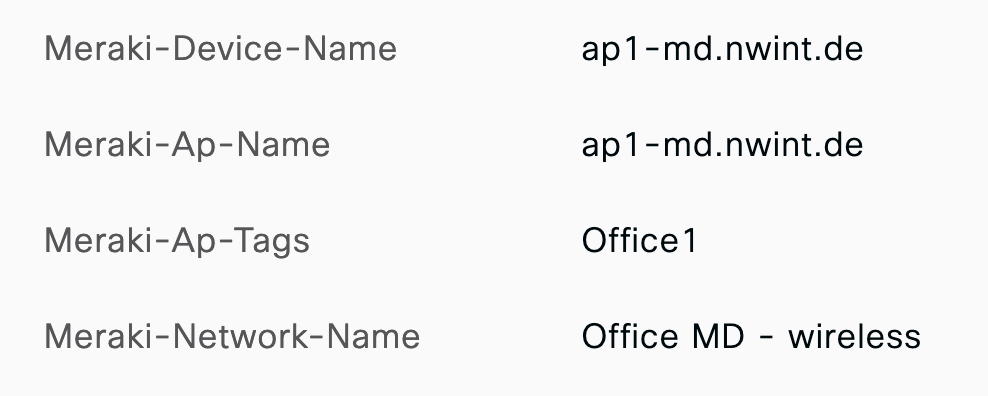
To show these correctly in the Logs, we need to import a RADIUS-Dictionry into the ISE:
VENDOR Meraki 29671
BEGIN-VENDOR Meraki
ATTRIBUTE Meraki-Device-Name 1 string BOTH
ATTRIBUTE Meraki-Network-Name 2 string BOTH
ATTRIBUTE Meraki-Ap-Name 3 string BOTH
ATTRIBUTE Meraki-Ap-Tags 4 string BOTH
END-VENDOR Meraki
These lines are copied to a file and can be imported into the ISE:
Policy -> Policy Elements -> Dictionaries -> System -> RADIUS -> RADIUS Vendors
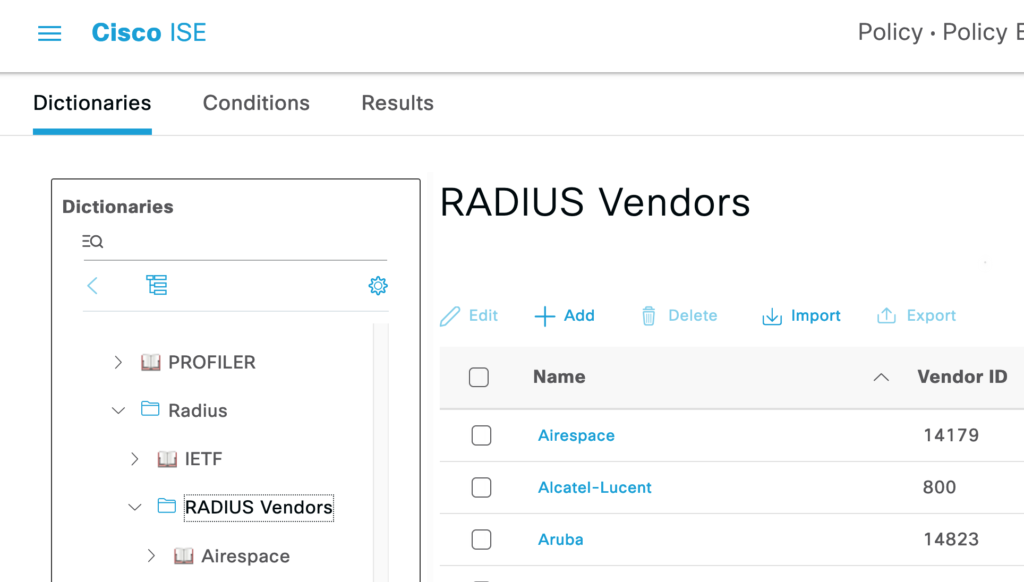
After the import, it should look like this:
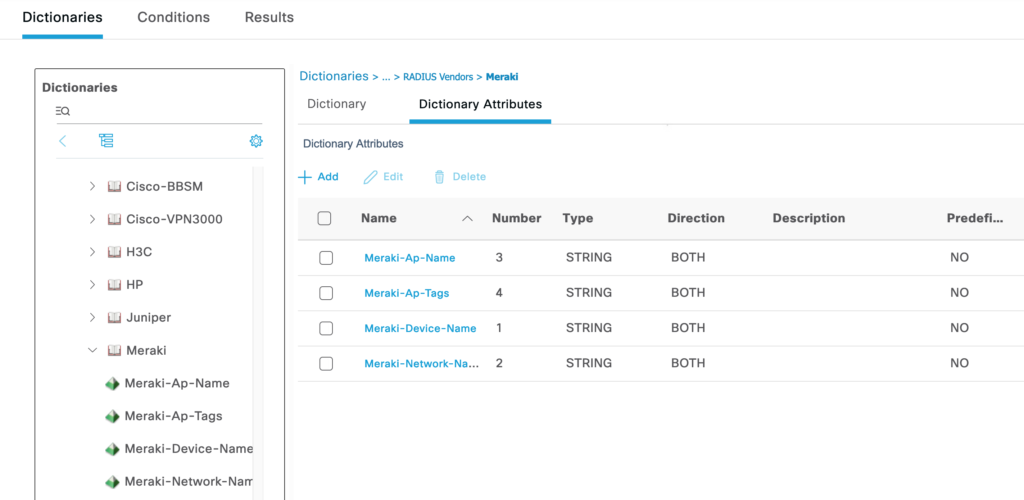
RADIUS Attributes from RFC7268 “RADIUS Attributes for IEEE 802 Networks”
Meraki APs send four Attributes that look like the following in the Log:
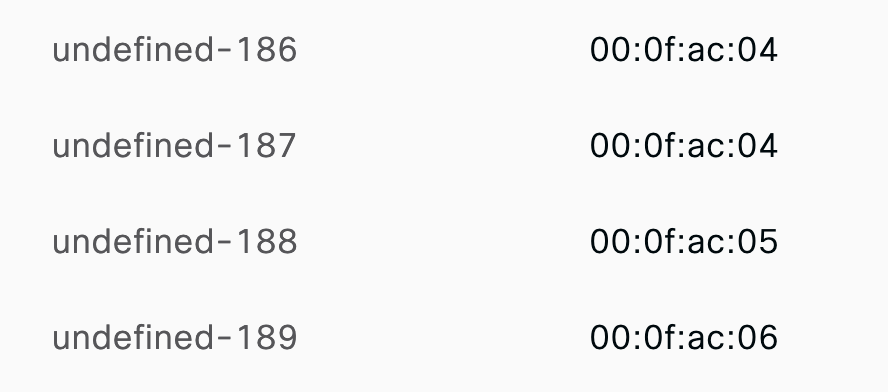
Not only the ISE has no knowledge of these RADIUS attributes, Wireshark 3.6.7 also shows them as “Unknown-Attribute”:
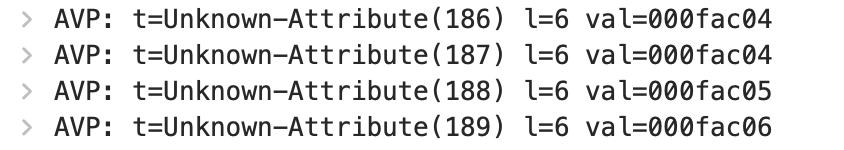
RFC7268 from July 2014 defines them as the following:
- WLAN-Pairwise-Cipher - WLAN-Group-Cipher - WLAN-AKM-Suite - WLAN-Group-Mgmt-Cipher EDIT: Meraki APs also send the Attribute 177 "Mobility-Domain-Id"
On the ISE, we can easily change the corresponding “undefined-xyz” attributes to the real names of the attributes:
Policy -> Policy Elements -> Dictionaries -> System -> RADIUS -> IETF -> undefined-xyz
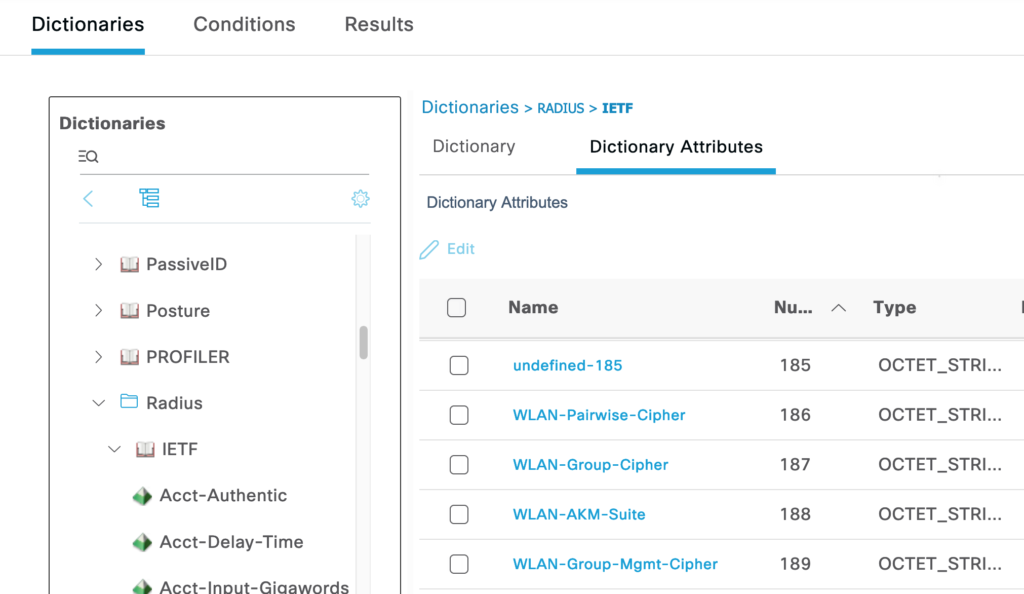
And now the ISE-logs are more meaningful:
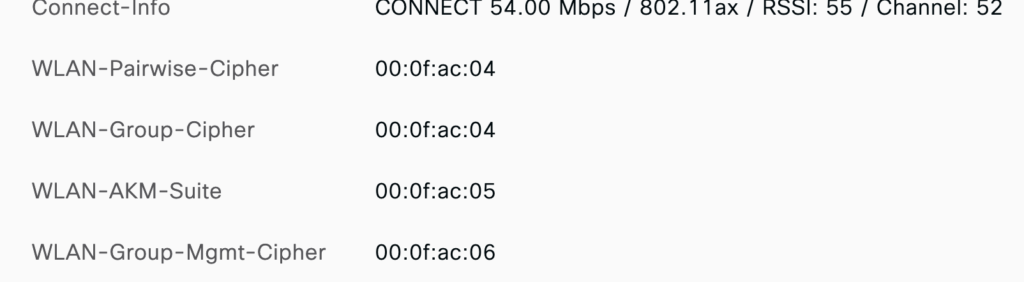
I still have to find out how I can replace the values with the corresponding names:
00:0f:ac:04 -> CCMP-128
00:0f:ac:05 -> 802.1X (SHA-256)
00:0f:ac:06 -> BIP-CMAC-128
If I figure this out later, or someone has a hint for me, I’ll add it to this blog-post.
Have fun with your Meraki/ISE combination!

One Reply to “Tuning the Cisco ISE for Meraki Networks”