Transition Disable is a mechanism to protect a WPA3 network against downgrade attacks and is described in Chapter 8 of the WPA3 Specification 3.3. When this feature is enabled, a station should configure it’s network profile to not connect to the SSID with AKMs that are not allowed in WPA3-only networks:
Transition Disable is an indication from an AP to a STA, that the STA is to not allow certain security parameters in the STA’s Network Profile (such that the Network Profile is no longer configured in certain transition modes) for subsequent (re)associations to the AP’s network.
WPA3™ Specification v3.3 – 8.1 Transition Disable Overview
Conclusion first
Does this fesature work? Well, perhaps, a little bit.
Implementation
On the Cisco 9800 WLC, this feature is supported starting version 17.7.1 and is activated with a single check box:
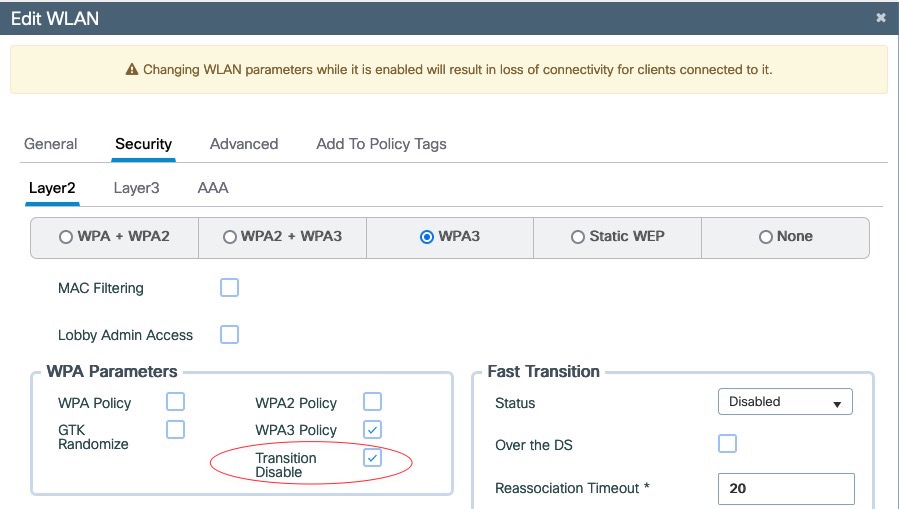
After activating Transition Disable, nothing changes in the Beacons or the Association. This feature is announced in a new Key Data Encapsulation (KDE) that is added to message 3 of the 4-way handshake. As this information is communicated in an encrypted form, I configured my SSID for WPA3 Enterprise. The Radioactive Trace on the 9800 provides the MSK from the EAP exchange that can be entered into Wireshark:
2024/03/13 09:42:52.050145900 {wncd_x_R0-0}{1}: [aaa-attr-inf] [18498]: (info): Applying Attribute : eap-msk 0 10 92 02 f9 96 0c fd 1b 37 f5 c0 00 69 f1 22 67 00 2e d6 53 2f aa 06 fa fe c2 52 c9 ab 85 bc 2b 78 ec 91 50 80 0c 22 39 7f 07 96 bd 64 f6 e5 50 60 48 2c be b8 a0 da 02 22 29 a0 62 66 39 4c ebThis is message 3 of the 4 way handshake:
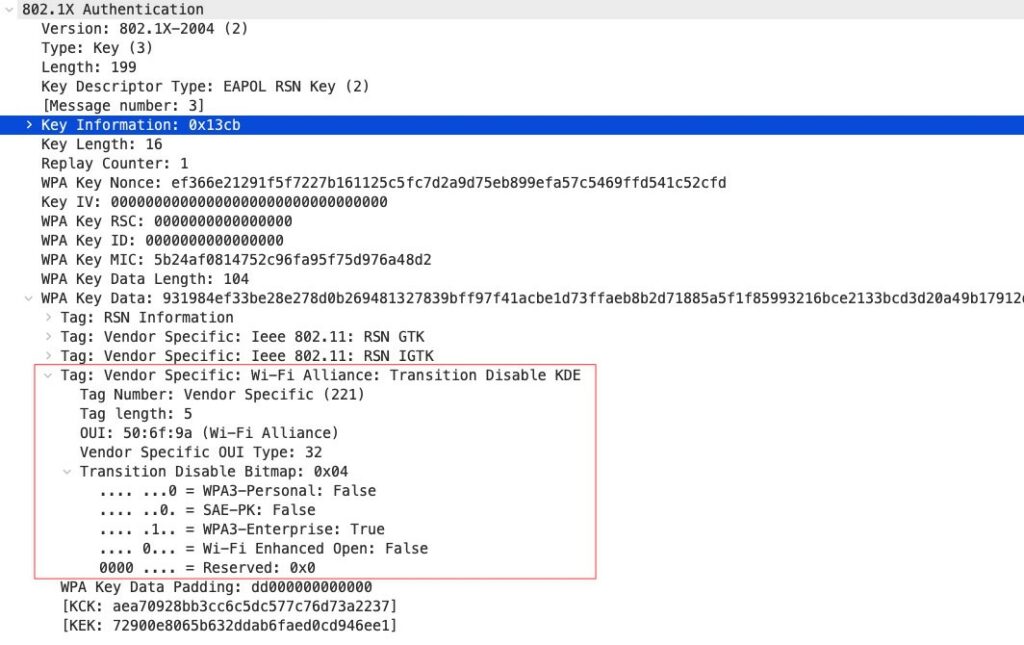
The Vendor specific OUI and type is not documented in the IEEE 802.11 standard, this is defined in the WPA3 specification from the Wi-Fi Alliance. The bitmap shows that this is a WPA3-Enterprise SSID that has Transition Disable configured.
Testing this Feature
My iPhone 15Pro with iOS 17.4 connected without problems.
After this connection, I reconfigured the SSID to transition mode which is a supported use case for Transition Disable. WPA3 devices are protected from downgrade attacks, but devices only supporting WPA2 with AKM 1 will not see this additional element.
As expected, the iPhone connected without any problem.
The last test was to change the SSID to only WPA2 with AKM 1. The purpose of this feature is to prohibit the end device from connecting to this SSID as this would be a clear downgrade.
Sadly, my iPhone connected again without any problems. It seems that this feature is not implemented in iOS.
More Tests
Is this only the iPhone?
For the next test I configured a new SSID with WPA3-SAE and transition disabled:
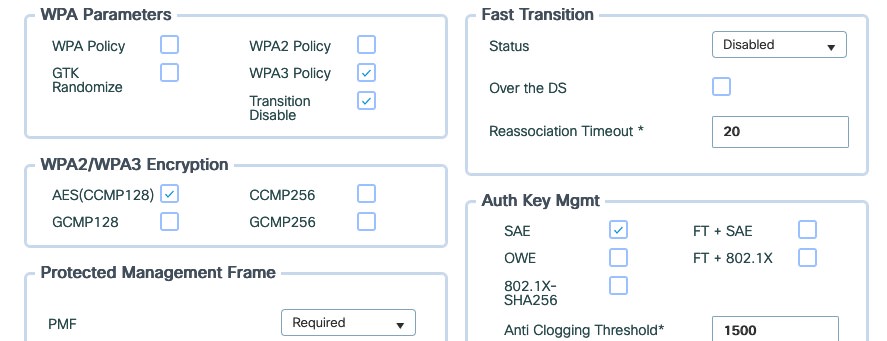
My test devices all connect without any problems:
- Mac Studio 2023 with macOS 14.3.1
- iPhone 15 Pro with iOS 17.4
- Samsung Galaxy Tab S7 with Android 13
- MS Surface Pro 8 with Windows 11 Pro 23H2
Then I reconfigured the SSID for pure WPA2 PSK. The purpose of Transition Disable is that the client should know that it should not connect to this SSID any more with the legacy AKM 2. The result was not showing a consistent picture:
- iPhone connects
- Android asks for the Passphrase and connects
- Win11 asks for the Passphrase and connects on the second try.
- Mac Studio asks for the Passphrase and does not connect. The PCAP doesn’t show any connection attempt. But when changing back to WPA3, macOS connects after a warning that the security of this SSID has changed.
This looks like macOS supports Transition Disable. But if it really does, it shouldn’t ask for a Passphrase if it knows that it won’t connect.
All in all, we can say that WPA3 Transition Disable is not yet a useful feature. Let’s see if this changes in the future.
EDIT 2024-03-28: Another Test
A discussion with Phil Morgan pointed out that a different test should be done. What happens when the Client only sees a different AP with the same SSID and WPA2 instead of the same AP reconfigured for WPA2.
- I again connected the iPhone and the GalaxyTab to the WPA3 SSID with Transition Disable to make sure the client has the SSID saved.
- The SSID on the 9800 was disabled
- I configured the same SSID with WPA2 on my Meraki AP
Both the GalaxyTab and the iPhone connected without problems. But on the iPhone there was a difference. After disabling the SSID on the original AP, it showed up under “other Networks” instead of “My Networks”. But still, it connected.
Again a confusing result.
