
Yes, I am one of the people who enter a building and look up to spot the Access-Points. As a wireless engineer you can:
- Learn something: “Oh, that’s a good approach!”
- Think about something: “Why did they do it this way?”
- And laugh: “Oh, how dumb. That doesn’t make any sense!”
And sometimes a 3) turns into a 1) “Ahh, that’s the reason; now it makes sense!”
And part of this crazy notion is to evaluate the WLAN in hotels when I am abroad. I always have my Nomad with me, just as some other crazy wireless engineers always carry their Sidekick with them.
A couple of weeks ago, I was staying at a hotel in London, and you can guess the Wi-Fi was not good. When traveling throughout Europe, luckily, I don’t have to depend on a good wireless connection, as cellular connectivity is mostly good and roaming is typically free. But for a visitor from a non-EU country, this can be a major pain point. And sometimes, even the cellular signal is very weak, and a good guest Wi-Fi is crucial.
Why was the WLAN in this hotel so bad? Many factors contribute to this, and in this hotel, these were the major problems:
- Unmodified Basic Rates. On 2.4 GHz, the minimum Basis Rate was set to 1 MBit/s. WiFiExplorer Pro showed zero or only a small number of clients on most APs, but the utilization was typically between 30 and 40 percent. Luckily, the channels were only 20 MHz wide, and the APs were distributed on channels 1/6/11.
- For the 5 GHz band, there was a mix of Wi-Fi 4 and Wi-Fi 5 APs. The Wi-Fi 4 APs used 40 MHz channels while the Wi-Fi 5 APs were configured to use 80 MHz channels. This showed the interesting effect that the Wi-Fi 5 APs had a much larger client count than the Wi-Fi 4 APs. Clients tend to prefer APs with weaker RSSI if the potential bandwidth is higher.
- There were APs in the hallway above the ceiling. On my floor, there were two APs, as shown in the heatmap. Although the left AP was likely next to my room, the reception in my room was awful and similar to the AP at the end of the floor.
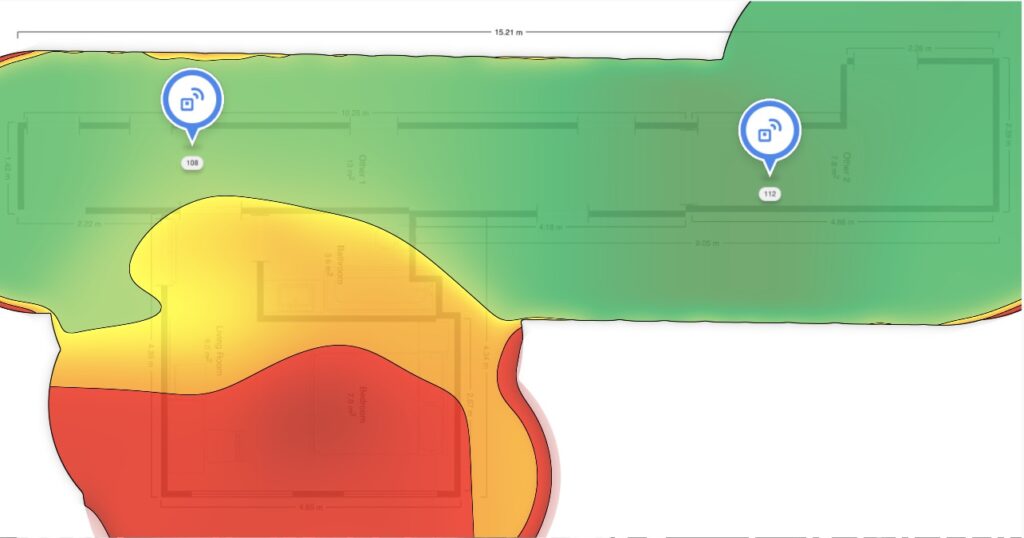
Was that all? No, there were more strange configurations, but they typically don’t contribute to the Bad-Fi experience:
- The Guest SSIDs were configured with 802.11v, but 802.11k was missing. This is at least uncommon.
- The corporate SSID for mobile devices was configured with PSK security and adaptive Fast BSS Transitioning. This likely doesn’t hurt, but it has a nearly zero effect. Given that the equipment was quite old, I would expect that the firmware was not patched against the vulnerabilities of PSK networks with FT.
- And last but not least: TKIP was the group cipher that should not be used today. Never, ever! Not even on a guest network. However, this is irrelevant from a security perspective on a network where every guest knows the passphrase.
All in all, it suggests that the operator or installer did not really know what he was doing there.
Sadly, this is not the exception, and most of the times the WLAN is not really good.
I advise all hotel managers who hire people or companies for their WLAN to get confirmation that all people working on the project are at least CWNA certified. Yes, as a CWNP instructor, I am a little bit biased. But this makes sure they at least know how WLANs work. And no, I don’t think that vendor certifications help here in any way. And also no, I don’t say that engineers without a CWNA can’t be good, it’s just that someone with at least a CWNA is less likely to propose bad things.
Happy traveling with great Wi-Fi!

One Reply to “The need for better Hotel Wi-Fi”